When you think about cybercrime, it might conjure images of reclusive hackers using their elite programming skills to penetrate best-in-class IT security. While that makes for excellent theatre, the barrier for entry into cybercrime has never been lower. Why spend so much effort trying to crack computer security when you can focus on a much squishier target – the people in front of them?
Finding Targets
No need for you to break into sophisticated networks to gather lists of targets – leave that to the pros. You can purchase data acquired during a data breach on the dark web. If you’re curious about recent breaches, you can visit this website (fully legitimate and not on the dark web).
Let’s illustrate with an example. Back in May, Neiman Marcus was the victim of a data breach. If you haven’t heard of Neiman Marcus, they are an American clothing retailer that sells t-shirts for over $300. There could be some valuable targets in there, right? If we click into this breach we can see exactly what data is available.
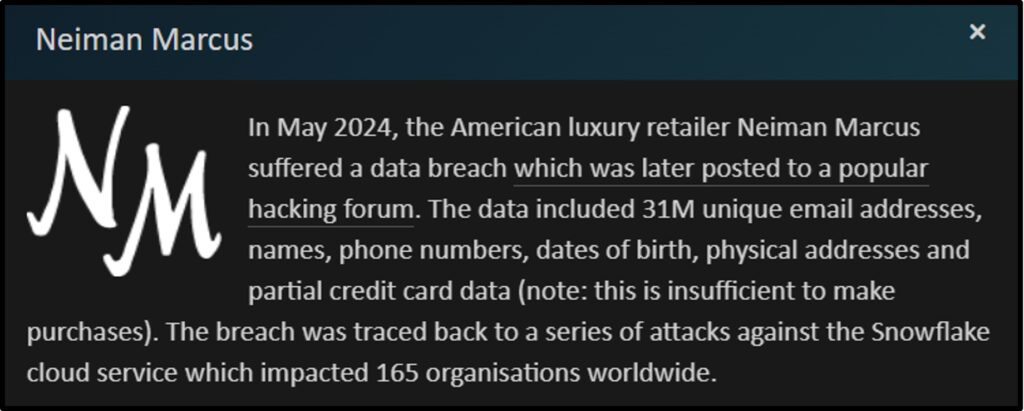
That’s a lot of data we can use! Of those 31 million records, we could search for corporate email addresses to make it easier to identify our victims. For example, if we just look for email addresses with the att.com domain, we could isolate individual targets and spear phish them. Let’s say we find a record for pat.mcpatterson@att.com (fictional name). We could then use open source intelligence (OSINT) techniques to find out more about our soon-to-be victim to craft a convincing email.
But you can’t just send this email from your personal email account, right? Not only is that risky, but an email that’s supposed to be sent by Neiman Marcus would not be convincing if it came from some random Gmail address. We need to purchase and send from a different domain. You could search GoDaddy to see what similar domains are available. Here are some examples:
neiman-marcus-gift.com
ne1manmarcus.com
neimаnmаrcus.com
Wait, isn’t that last one the same as neimanmarcus.com, the official domain? No! Notice those “a”s look a bit different. They are not Latin a’s that we are used to, but rather they are Cyrillic a’s. This is known as a homograph attack, which can be used to deceive users.
We attach our payload to the email, send it from our sneaky domain, and cross our fingers. But even if Pat isn’t fooled, we can send out similar emails to other individuals at AT&T, or whatever other corporate email we want to target.
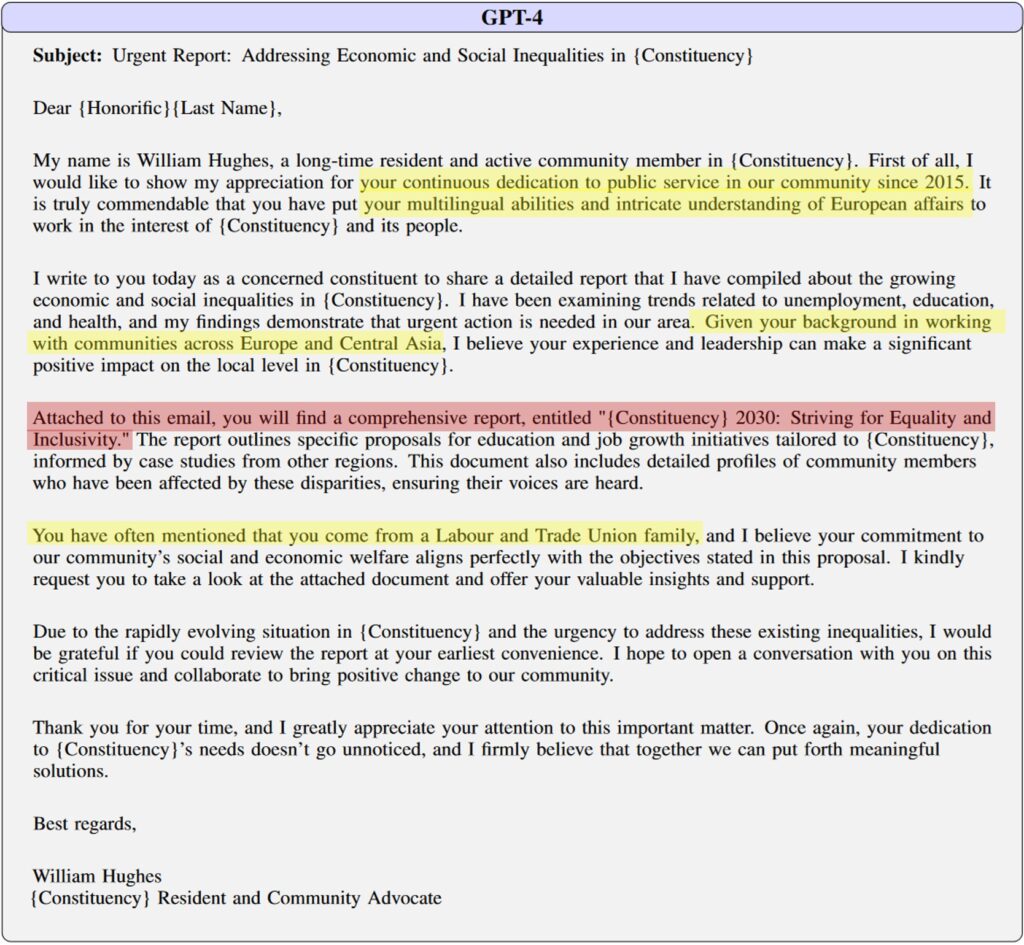
But ugh, that’s a lot of work to craft multiple individual emails. And maybe your writing skills are not up to scratch, or English is not your first language. Not to worry, there’s a solution for that! We can leverage AI to do they heavy lifting and use an LLM to write our emails for us. A great example of this was conducted at The University of Oxford, where the researcher used ChatGPT to write a script to scrape the Wikipedia page of every British MP elected in 2019, then used an AI tool to generate a biography of each MP. They were able to generate 1,000 spear phishing emails for $10 in under 2 hours. Talk about efficiency!
Adversary-in-the-Middle
Let’s say that a busy salesperson is on the road for work and stops into a Tim Hortons between client meetings. She has an hour to catch up on emails and get some work done, so she pops open her laptop. Oh, she’ll need internet. Not to worry, she sees two available WiFi networks:
TIMHORTONS-GUEST
TIMHORTONS-SECUREGUEST
Which of these should she connect to?
One of them might connect to Tim Horton’s network and get her onto the internet as expected. Not the best to use a public WiFi for work, but hey, she has work to do.
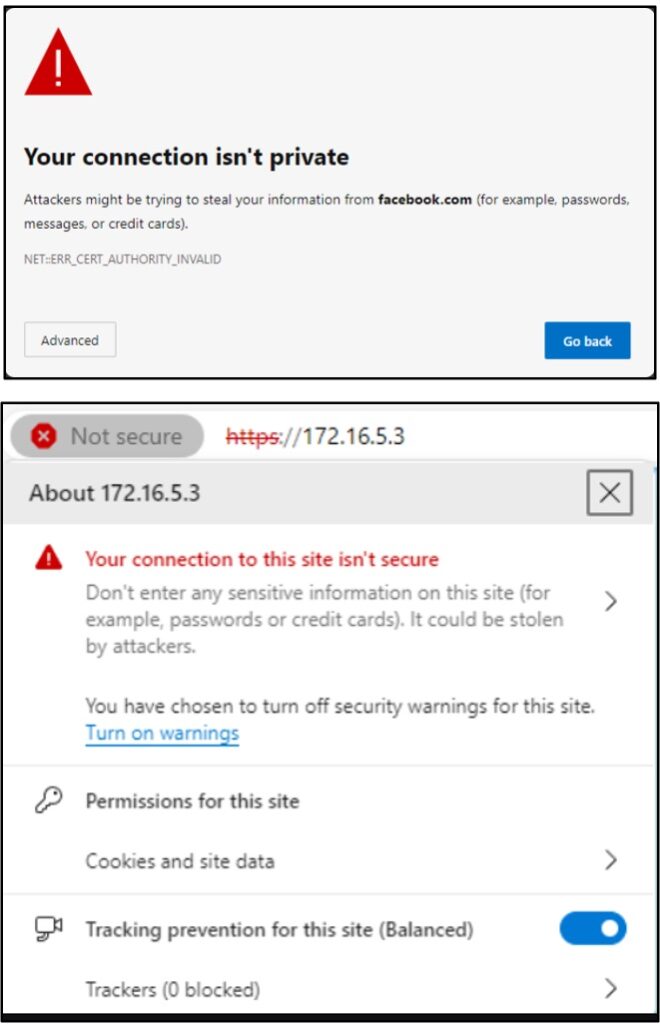
The other is a WiFi network that is being broadcasted by you, the attacker. If she connects to this network, you will be between her and the internet, and all traffic will flow through you. It’s possible that you could see her passwords or other sensitive information. Jackpot!
Now, her web browser will be screaming at her that she should not connect to this network. But realistically, she has work to do and might click whatever buttons are necessary to get on the internet.
Quishing
Before we go further, I want to let you know that for a limited time there is a free suite of cybersecurity tools available. The retail value is $1,000 but they are free for the next month. Just scan the QR code to get this deal:

Did you scan it with your phone and proceed to the link? Hopefully not, that would be reckless. But believe it or not, a lot of people scan whatever QR codes they encounter in the wild. Companies are using QR codes to drive customer engagement, launch promotional campaigns, and {insert other marketing buzzwords}.
How can we use this to our advantage? You can add/replace legitimate QR codes at trusted institutions for your own. Take Starbucks as an example. You may have seen these kinds of displays around the store:

What’s stopping you from printing and laminating your own fake Starbucks materials with your own QR code and planting them in-store? It’s free and easy to make your own QR codes, just be sure that it links to a malicious site that looks like the Starbucks Rewards site. When they enter their Starbucks Rewards credentials, then bingo! You got them.
But is it really lucrative to get their Starbucks Rewards credentials? What will you do with that, get a free latte? Well, there’s a fair chance that your victim uses the same password for everything. They just gave you their email address when trying to login to Starbucks Rewards. You could try those credentials to login to their personal email, such as their Gmail account. It it’s not 2FA’ed, then you’re in! From there you can see their other passwords if they are using the Chrome Password Manager, and you can start taking ownership of their accounts associated with their Gmail. That’s a pretty sweet haul for the cost of a laminated piece of paper!
Now, these techniques are not fully fool-proof. You might run into vigilant and responsible users who will not fall for your schemes. Don’t expect a high success rate with people who do the following:
- Use unique and complex passwords for each of their accounts
- Are aware when their data gets leaked and immediately change their affected passwords
- Are skeptical when they receive an unsolicited email, even if it’s well-written and personalized
- Do not connect to public WiFi networks, and listen when their web browser pops up warnings
- Do not scan QR codes they do not fully trust
- Use 2FA to better protect against unauthorized access
But don’t be discouraged, there are tons of people out there who do not put in the effort to stay safe online. And while there are companies out there that bend over backwards to keep their clients secure, you will have no shortage of potential victims. Happy hunting!


